07. Security Trends Exercise
Security Trends Exercises
Exercise #1 - Instructions
Cybersecurity incidents and data breaches are now a part of our lives. The website Information is Beautiful provides a visualization of recent cyber events.
Step 1: Go to the Information is Beautiful World's Biggest Data Breaches & Hacks website. Scroll down the page to view data breaches. The size of the breach is indicated by the size of the bubble.
Step 2: Pick a recent event and click on its bubble. Review what happened.
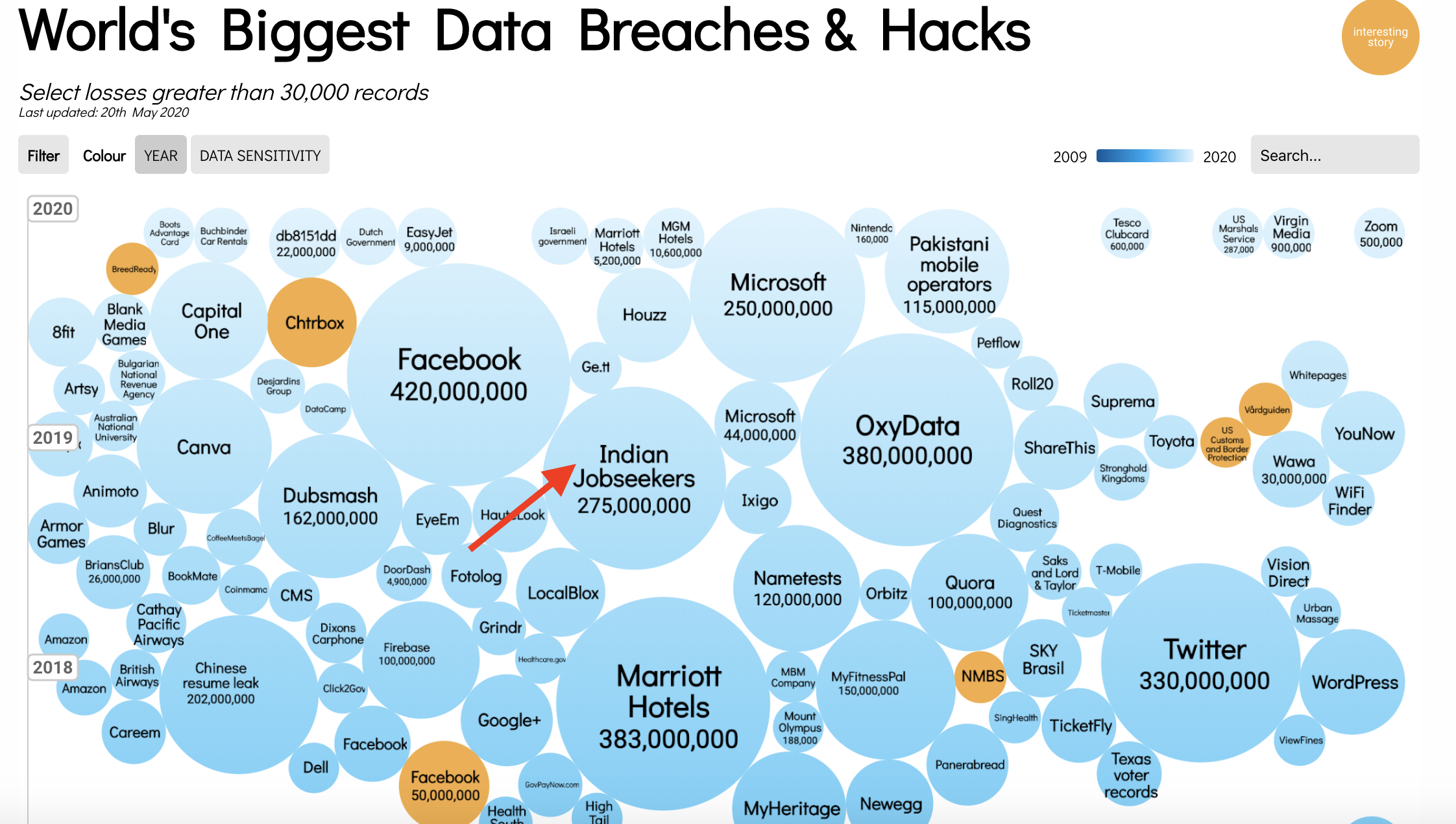
Reflect on Security Trends - Information is Beautiful
QUESTION:
For the data breach you selected on the Information is Beautiful, reflect on what happened, who is or was affected, and how it happened (if known).
ANSWER:
The intent of this exercise is for you to explore the Information is Beautiful website collection of recent data breaches.
For example, in the Marriott data breach of 2018, malicious hackers attacked their Starwood reservation system exposing personal data for up to 500 million of their guests. The names, addresses, phone numbers, birth dates, email addresses, and encrypted credit card details of hotel customers were stolen. The travel histories and passport numbers of a smaller group of guests were also taken. The article does not say how the data may have been stolen.
Exercise #2 - Instructions
Another resource with information on recent data breaches is the Verizon Data Breach Investigations Report (DBIR). For over 12 years, the report provides an analysis of data breach trends affecting a variety of sectors, including public administration, healthcare, and education.
Step 1: Go to the Verizon DBIR website and view the Executive Summary from the most recent report. You may also want to look through the entire report. The Verizon DBIR provides quantitative data on recent breaches.
Step 2: From the Executive Summary, answer the questions below. The intent is to get you into the report and familiar with its contents.
Reflect on Security Trends - Verizon DBIR
QUESTION:
From the Verizon DBIR you selected, answer the following:
- Who is behind the attacks? Explain the general categories rather than specific threat actors.
- What actions are being used?
- Who are the breach victims?
ANSWER:
From the 2020 Verizon Data Breach Investigations Report:
- 70% of attacks were perpetrated by outsiders and 34% involved internal actors.
- 45% of breaches featured Hacking, 22% included social attacks, and 17% involved malware. 86% of the breaches were financially motivated
- 72% of victims were large businesses and 28% were small businesses.
Even though these values change over time, the general concepts have remained steady. Take time to understand this report as it's used throughout the cybersecurity industry.